what is access control entry
What Is Access Control Entry? Types, Benefits & How It Works
What is access control entry? It’s a security system that controls who can access a particular area by using methods like biometrics, passwords, and keycards to verify identities. These systems limit unauthorized access and log entries by providing strong security.
Each type of system from role-based to discretionary and mandatory access control meets distinct security requirements. Additional security is provided by features like smart cards and biometrics. Access control improves overall security, reduces theft, aids compliance, and allows remote monitoring. These features make it a crucial option for businesses that prioritize both efficiency and safety.
What is Access Control Entry?
Access control entry is a way to manage and control who can enter a particular area. This ensures that only authorized individuals can enter secure areas because the system restricts access to unauthorized people,
It operates by verifying identities through various methods such as keycards, passwords, biometrics, or smart devices. Access control strengthens security by limiting unauthorized access. It also keeps a record of entries and exits which allows for better control over secure areas. Organizations that place a high priority on the safety and security of their employees or assets should have an access control entry system.
How Does Access Control Entry Work?
- Identification Verification: The first step in access control is to identify the individual trying to enter, typically through ID cards, biometrics, or PIN codes. Only authorized individuals pass this verification.
- Authentication Check: The system checks the user’s identity and confirms if they have the required credentials to access the designated area. This adds an important security layer.
- Access Grant or Denial: After verification, the system grants or denies access based on the person’s credentials. This immediate decision ensures entry points remain secure.
- Logging of Entry: Each entry attempt is automatically logged. This creates a detailed record of who accessed specific areas when they did so, and for how long. This is valuable for audits and tracking.
- Continuous Monitoring: Many systems continuously monitor entry points and issue alerts if an unauthorized access attempt occurs. This strengthens overall security.
Types of Access Control Entry
Access control entry systems provide various ways to control and monitor entry into secure areas. Here are the main types:
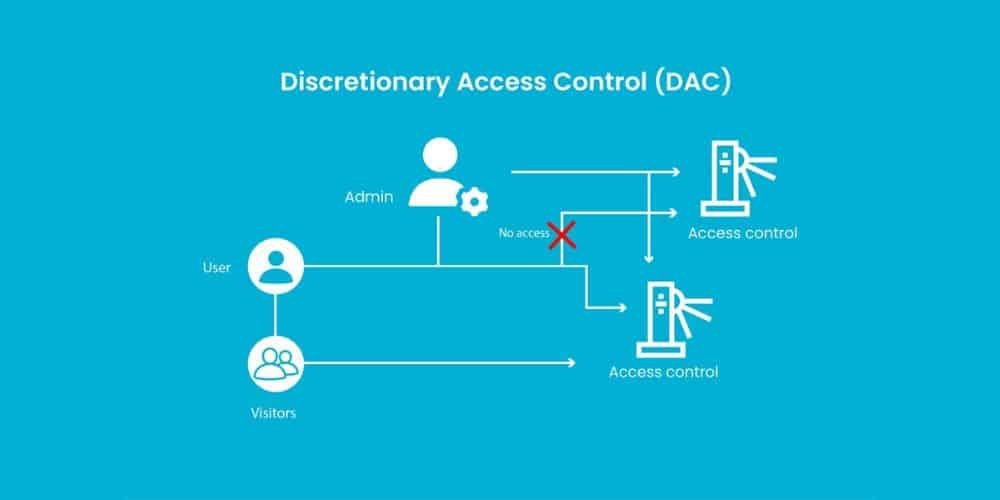
1. Discretionary Access Control (DAC):
DAC lets the owner or manager of a secure area set permissions. This allows them to choose who can access certain resources. This type provides flexibility as access permissions can be adjusted as needed by the owner which allows for easy management.
However, it requires careful oversight to prevent unauthorized access if permissions are granted too freely. Organizations where managing individual access levels is crucial are more likely to use DAC.
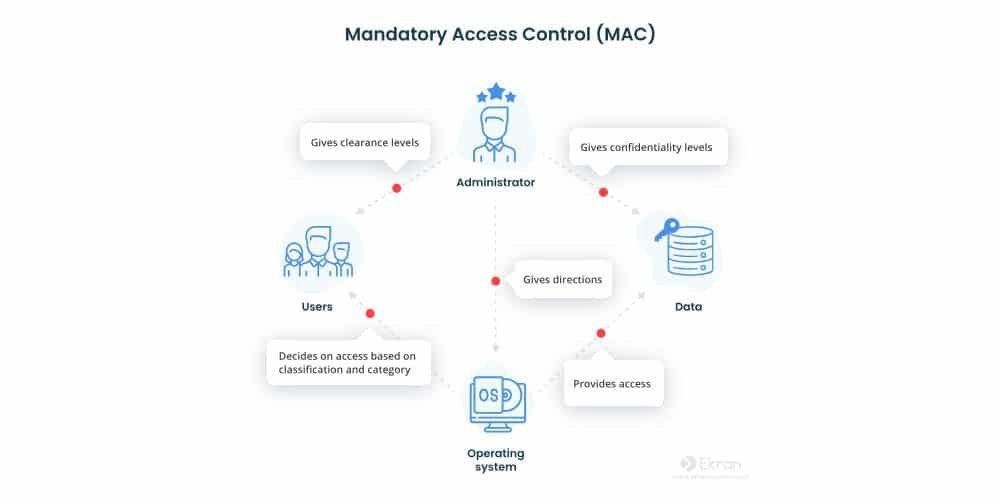
2. Mandatory Access Control (MAC):
MAC (Mandatory Access Control) is a more secure system that controls access permissions from a central place, and individual users can’t change these settings. Security clearances are given based on set rules, and this ensures that only authorized personnel can access sensitive areas.
MAC is ideal for high-security environments such as government agencies, where strict access rules are mandatory to maintain confidentiality and security.
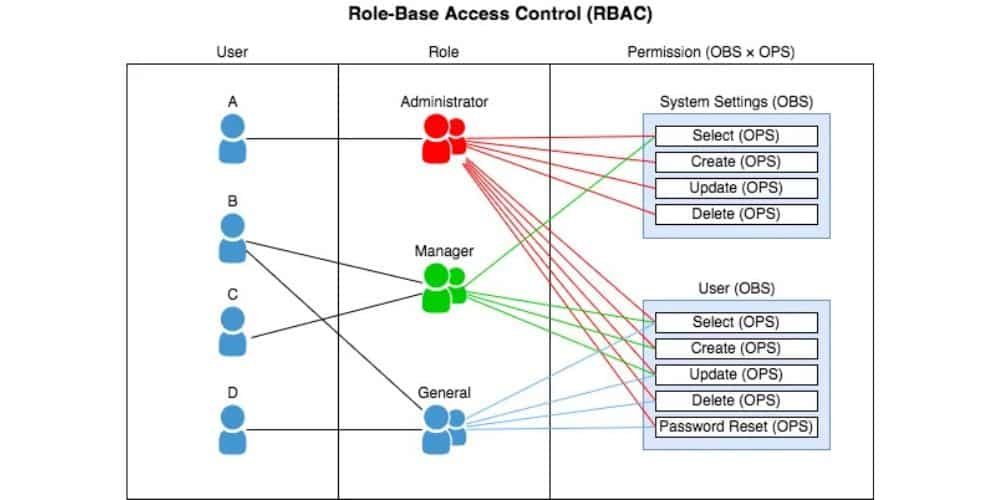
3. Role-Based Access Control (RBAC)
In RBAC, permissions are assigned according to roles within the organization. Employees are given access to areas needed for their specific duties, which ensures efficient and secure access management.
This approach is widely used in corporate settings to simplify access control and reduce administrative work while keeping strong security.
4. Rule-Based Access Control
This type uses specific rules to determine access permissions, such as time-based rules or location-based restrictions. This system is ideal for businesses that need flexible control. Permissions can be customized to allow or restrict access based on factors like working hours or event schedules. This approach improves security systems while fulfilling operational needs.

5. Biometric Access Control
Biometric access control systems use unique physical features, like fingerprints, face recognition, or eye scans, to verify users. Biometrics offers high security because these features are hard to copy, which makes unauthorized access almost impossible. Biometric systems are commonly implemented in facilities requiring top-level security.

6. Smart Card Access Control
This system uses smart cards with chips to check identities and allow secure access. Smart cards provide a convenient way to manage access and can store additional data like attendance records. They are especially popular in office buildings and large facilities for secure and easy employee entry.

7. Keypad Entry Systems
Keypad systems require users to enter a unique PIN code to gain entry. This approach is straightforward, cost-effective, and easy to implement. It is commonly used in smaller facilities or areas with moderate security needs, keypad systems add a reliable layer of security to any access control setup.
Importance of Regular Maintenance in Access Control Systems
Regular maintenance is crucial to keep access control systems reliable and effective. Regular maintenance guarantees that each component, including software and physical entry points, operates at its best. Maintenance includes checking for software updates and testing authentication methods. It also involves verifying that all security logs and access records are accurate and accessible.
Maintaining the system regularly minimizes the risk of malfunctions or unauthorized access. It also helps reveal potential weaknesses, which allows for timely upgrades or repairs by addressing issues early. Regular maintenance strengthens an organization’s security protocols and ensures smooth access for authorized personnel. This approach builds trust among both employees and clients. Reliable maintenance also extends the system’s life.
The Benefits of Access Control Entry
Implementing an access control system provides multiple advantages for security, efficiency, and management. Key benefits include:
1. Enhanced Security
Access control systems ensure that only authorized people enter restricted areas.
This lowers the risk of trespassing, theft, and vandalism. It makes secure spaces safer for both personnel and assets. These systems also remove the necessity for continuous monitoring by humans automating verification.
2. Efficient Access Management
You can manage permissions seamlessly through access control. Authorized personnel can access necessary areas quickly without delays which improves overall workflow and efficiency. Access permissions are easy to update so that organizations can adapt to changes without complicated adjustments.
3. Reduced Risk of Theft and Damage
Access control systems reduce the chance of both internal and external theft by restricting entry to specific people. Restricted access also minimizes the risk of accidental or intentional property damage which saves costs and preserves valuable assets.
4. Improved Compliance
Access control systems help organizations follow security rules by controlling who can enter. Many industries require access records for audits and legal compliance, and these systems provide an accurate and automated log. It reduces liability and enhances accountability.
This reduces liability and improves accountability by keeping a clear record of who accessed secure areas and when. Organizations can ensure compliance with regulatory standards through detailed tracking and quickly provide necessary information for audits.
5. Detailed Entry Logs
Access control entry systems maintain comprehensive records of every entry and exit. It provides information about who visited particular locations and when. These logs are important for investigations, audits, and maintaining organizational transparency.
They provide a clear record that improves accountability and allows for accurate tracking of all movements within secure areas. In case of any incidents, these detailed logs can support timely investigations and help to prevent future security issues.
6. Remote Access and Control
Modern access control systems allow remote management. This enables administrators to monitor and control entry points from any location. This feature is particularly useful for multi-site operations and it ensures that security personnel can respond quickly to any potential breaches.
Remote access lets organizations update permissions right away. They can adjust access levels in real time to meet changing needs or handle security risks. This flexibility greatly enhances overall safety and operational efficiency.
Conclusion
Access control entry is an essential security measure that protects restricted areas by verifying identities through biometrics, keycards, and PINs. These systems protect assets and support compliance with flexible options like Role-Based and Biometric access. They also allow for remote management to improve security and convenience.
Adopting an access control system is a wise choice for any organization focused on safety and efficient operations. It provides reliable security, ensuring spaces stay protected with confidence.
